As many may have seen, the Administrator account has some special privileges. It can logon to a workstation/server when no Global Catalog is available and it can always logon. Well seems that always is not entirely true.
Just as a regular account the Administrator account gets locked when the password attempts reach the limit as defined in the Password Policy. However, a domain controller will unlock the account as soon as a valid password has been entered. (see Jorge’s blog) That way, you can never lock yourself out of the system. However, since also most malware makers know that, they can keep trying the admin password without waiting for the lockout duration time to expire. So sometimes (actually perhaps always) you want to make sure your Administrator account is locked for a certain time period when too many passwords have been attempted.
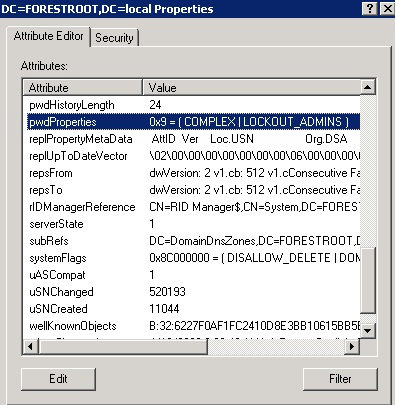
You can disable the auto lockout reset by setting the pwd-property attribute to value 8 or 9 (9 being disabled but require strong password). Go to Adsi Edit, right click the domain and set the pwd-property to 8 or 9 (depending on if you want complex passwords).
See more on: http://msdn.microsoft.com/en-us/library/ms679431(VS.85).aspx
(Thanks to Ned Pyle)
While conflicker is on the loose, many administrators see passwords dictionary attacks on their domain controllers. It seems many accounts are locked out due to these attacks. That led to new insights in how lockout policies must be applied. If you have a good monitoring system that can also monitor password guessing attempts, it would be easy to filter 5 passwords within 5 minutes or 10 passwords within 5 seconds. Let that monitoring system disable/lock the account or inform staff. For more information on the effects of Conficker on the domain controller see the Directory Services blog).