Microsoft is on a quest to remove passwords. While this will be a long journey it is worth the effort. Passwords are weak as people tend to reuse their passwords on various sites and/or websites don’t do enough to protect them. And so, accounts are breached almost on weekly basis, and many passwords are “known” passwords today.
While Microsoft has the ability to detect “breached passwords” in Azure AD (with the right license), it would be better to remove the need for passwords altogether. And so Microsoft joined the FIDO movement. fIDo stands for Fast Identity Online and the 2 is for the 2nd factor. How it works in the backend you can read on John’s blog. This post focusses on the real-world implementation and which keys you can use.
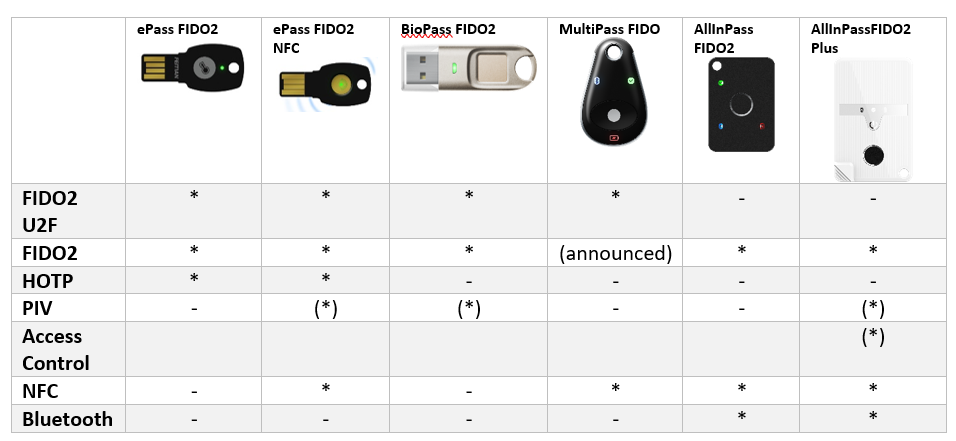
Given we want to remove passwords, we need something else to “proof” our identity. Within the Windows 10 eco-system you can use Windows Hello through PIN, Facial Recognition or Fingerprint. But what if you are not using Windows 10 but are on OSX or even your iPhone. What if you don’t have your laptop with you and are in an internet café. How do you then authenticate securely? This is where FIDO2 comes in. FIDO2 devices are small devices that provide USB, NFC or Bluebooth connections for you to interact with the system. The ones I have, use Fingerprint + PIN to authenticate me. And you can store multiple user accounts on them.

So, in order to authenticate now, you have to provide your key (something you have), something you know (PIN) and something you own (fingerprint). How secure do you want it?
When I want to authenticate to any Microsoft website and AAD dependent application, I use the FIDO2 key to authenticate me. And it’s not only for Microsoft related websites, in the right identity architecture you can use it for access to all corporate applications. This through the integration of applications to Azure AD. Including the corporate applications using Kerberos behind F5 or Azure AD Application Proxy. Or directly if the application supports FIDO2 keys directly. It’s just an additional account on the same key. But integrating it to Azure AD makes SSO easy.
My advice for companies already utilizing Azure AD (for O365/Azure/Dynamics) is to make sure all corporate applications are “linked” to AAD. Integrating the authentication for applications removes the need for users to have separate credentials for all those SaaS based applications like SalesForce, Box, GSuite, GitHub, LiveMeeting and many, many ,many, many more.
Before you get all excited
The FIDO2 features limits itself today for a few scenario’s only.
- Browser based authentication
- Windows 10 – Intune authentication
- Windows 10 – LiveID Account
That means you cannot use the key to sign into Windows 10 Home/Pro editions that are standalone with a local account or any domain joined device (yet…)
FIDO2 Keys by FEITIAN
This chapter is sponsored by FEITIAN who sent me their Passwordless Authentication Kit with all kinds of different keys

So instead of a username and password, users now have their token device. And depending on your/their preference this token device is a device you need to plugin to the computer/phone or a Bluetooth/NFC device you can pair with the device.
The FEITIAN kit has various models. Three USB-A devices, a USB-C device and 3 Bluetooth devices. Each device has its own characteristics and choosing a device might be cumbersome. In short, you can decide if you need USB (A or C). This does not require the device to be “paired” with the computer/phone and you can plug it into almost any device. They are smaller and fit simply on a keychain. The downside is, that USB only devices cannot be used in combination with your phone or iPad. For those you are probably better off using Bluetooth or NFC devices. Luckily there are also combinations of devices that allow you to do NFC and USB (A).

I’ve been using the BioPass FIDO2 for the last few weeks, and I must say I am impressed, with the only remark that the orientation of the USB port does affect the usability. For example, my Surface Pro 6 has a USB port on the right side of the screen. Making it easy for me to read my right-thumb fingerprint. But when I travel with my Surface Laptop 2, the USB port is located on the left on the base at the back. To read my fingerprint I have to pickup the laptop, move my arm in an awkward position just to read my thumbprint. Luckily you can add multiple fingerprints to the device and thus, I’ve added my left index finger to it as well.. just to make it easier…
Key Registration
There are multiple types of keys that you can distribute to your users. All keys use a PIN code and some add fingerprint security. The Feitian keys I used in this demo use fingerprint ID’s to ensure that they can only be used by me. When you have a device with Fingerprint support, you probably want to enroll it first. If your device does not support fingerprint, the initialization of the key can also be completed during the web-based registration for AAD.
While there are many ways to initiate it, I found the easiest was to use Windows 10 Sign-In options. After pairing the device (Bluetooth) or plugging it into the USB port, go to Sign-In options and select Security Key / Manage.
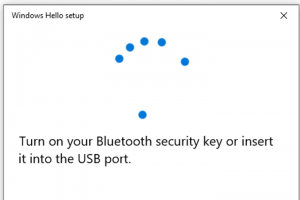
If you chose the Bluetooth version, click the powerbutton on the key and touch the fingerprint reader.
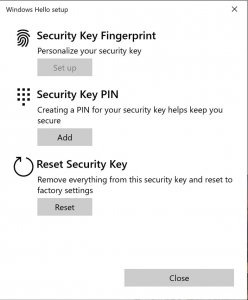
Click on Add to create a PIN for the device. This PIN is for the device itself and will be required every time you sign-in using it. Next, click on Set Up under the Security Key Fingerprint
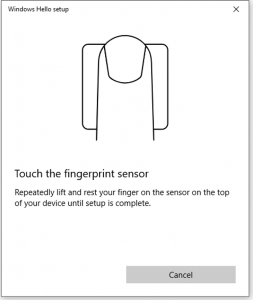
The device is ready for use now, so next is to enable the use of these FIDO2 devices in Azure AD.
Enabling keys in AAD
In order for AAD to “enable” FIDO2 keys, an administrator needs to authorize this for users. This can be enabled for all users or specific groups or users.
Login as the Global Admin to AAD and go to Security, Authentication Methods and select the FIDO2 Security Key. Select YES under enable and set your target to a group/users or all users. Enable Allow Self-Service setup.
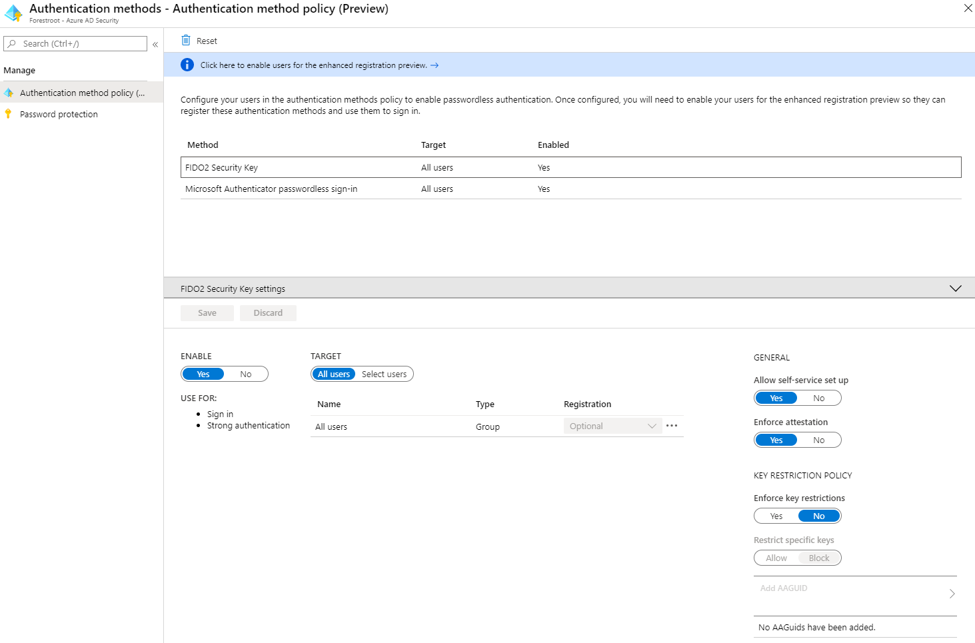
That’s all you have to do as an administrator
Adding the key to your AAD account
When users login (initially with their username/password), they can register a new key in their “security profile”. This option can be found through many ways, but I found the easiest was through myapps.microsoft.com then click your username on the right top and select profile.
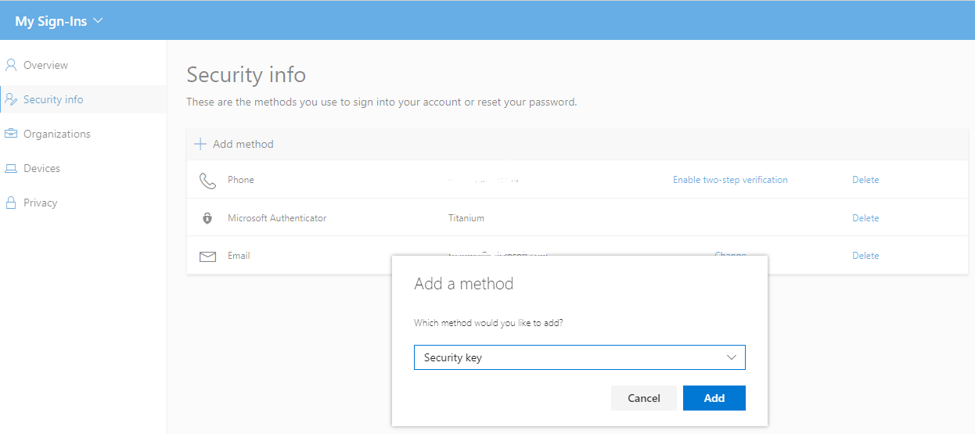
Click + add a method and select the security from the list. Next there will be a pop-up on what type of device you want to use (USB or NFC). If you are using Bluetooth devices, select USB.
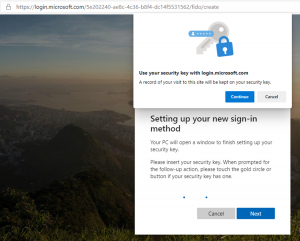
A security pop-up will be displayed to ensure you want to update your key, click continue. If you didn’t insert the FIDO2 key yet, a pop-up will be shown to insert it, or to power-on the Bluetooth device if you use that.
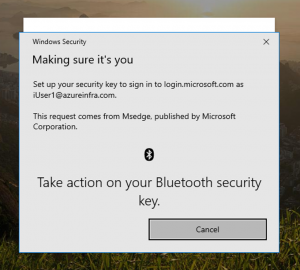
Once the key is recognized you need to “Take action on your key”- this usually means reading your fingerprint. If a PIN is also set (recommended), the next window will ask you for your PIN code (of the key). And you are set!
As the key is stored in your AAD security profile, you can give the key a name. If you loose the physical key, that allows you to delete it from your AAD security profile and render it completely useless for others (if they even had your fingerprint and pin code).
How to sign-in with a security key?
The next time you want to sign-in to any AAD linked website, you can select “Use a security-key”

Plug-in the USB FIDO Key or power-on the Bluetooth key, And put your finger on the fingerprint readere and you are singed in. It is that simple!.
The key is not “tied” to your device (except for the Bluetooth connection), so you should be able to use the same key on any device.